
Malware, intrusive software that is designed to damage and destroy computers and computer systems. Examples of common malware includes viruses, worms, trojan viruses, spyware, adware, and ransomware.
Computer Virus, a malicious software program loaded onto a user's computer without the user's knowledge and performs malicious actions.
Spyware, a category of software that steals personal information.
Computer Worm, a malicious, self-replicating software program that affects the functions of software and hardware programs.
Trojan Horse, a type of computer software that is camouflaged in the form of regular software that can kill background system processes, delete hard drive data and corrupt file allocation systems.
Keylogger, activity-monitoring software programs that give hackers access to your personal data.
Phishing, a scam where thieves attempt to steal personal or financial account information by sending deceptive electronic messages that trick unsuspecting consumers into disclosing personal information.
Rootkit, a clandestine computer program designed to provide continued privileged access to a computer while actively hiding its presence.
Adware, software that displays unwanted and irritating pop-up adverts which can appear on your computer or mobile device.
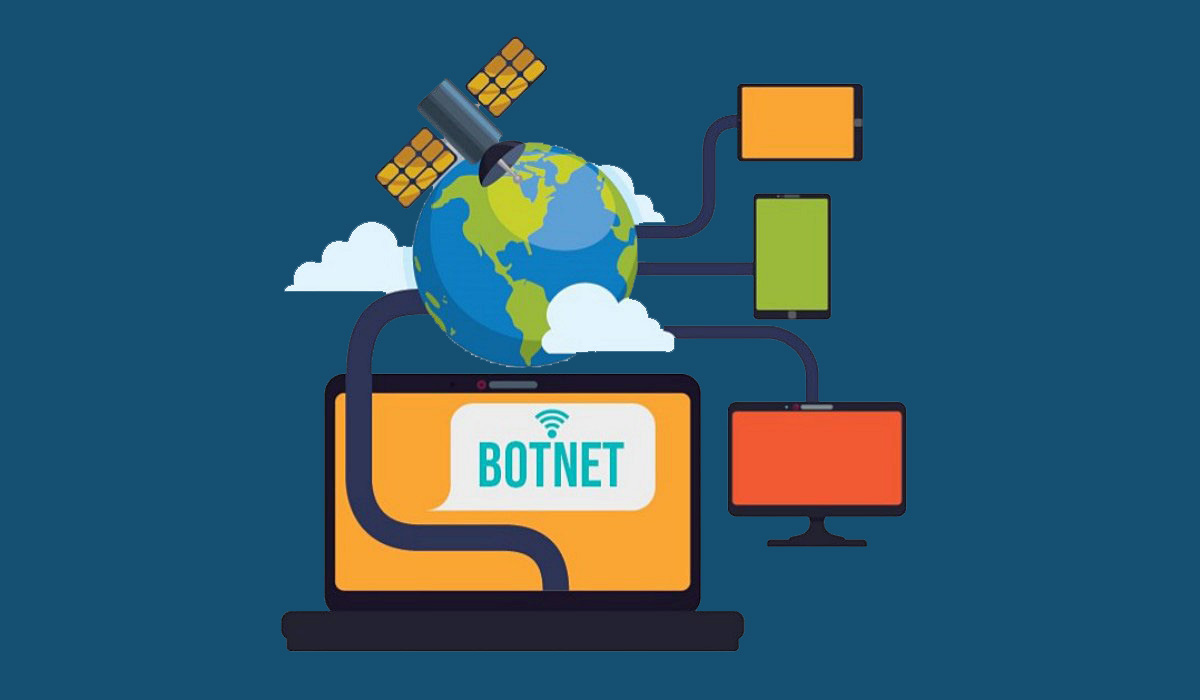
Botnet, a network of hijacked computers and devices infected with bot malware and remotely controlled by a hacker, used to carry out various scams and cyberattacks.
Fileless Malware, a type of malicious software that uses legitimate programs to infect a computer.
Ransomware, malware that employs encryption to hold a victim's digital information at ransom.
Clickjacking hijacks clicks of a user on a website which effectively translates into leading a user click on something malicious or sharing confidential information details he is not even aware of.
Browser Drive-by Attack, occurs when a user visits a compromised website and malicious code exploits weaknesses or other security vulnerabilities
in the user's web browser or browser plug-ins allowing the download of malicious files to the user's computer















MALWARE Agobot bagle bashlite bifrost blaster bohmini bolgimo boza brontok caribe cih code-red concept conficker cryptolocker ctx daprosy duqu explorerzip gameoverzeus graybird happy99 iloveyou kak kenzero koobface leap locky melissa memz mocmex morris morto mydoom mylife nimda flame laroux ngrbot nyxem nyxem pegasus petya ply psyo0t regin sadmind santy sasser shamoon shlayer skywiper sqlslammer sober sobig sql-slammer staog storm stration stuxnet swen tinba thanatos titanium torpig vbmania vundo wannacry waledac welchia witty xafecopy zeus zlob zotob

HOME
Columns:
Tech Fixed Nav
HTML CSS
Technology Stack
PHP JavaScript Python
SQL AJAX XML PERL
Five Six Seven Eight
Database 1+2+1
LLMs Expand
ADA Website Compliance
Dyslexic Guidelines
OSI Model
Layouts:
Dark Web 1+2 Layout
Protocols 1+3 Layout
Malware 1+4 Layout
Code Sharing 2+4 Layout
Search Engines 3+1 Layout
Custom ROMs 4+1 Layout
AI Websites 4+2 Layout
Offset 70-30 Layout
Cloud Services 1+2
Top Level Domains
ZigZag Layout
Database:
Database Select Query
Database Sort Query
Database Select Europe
Database Select Japan
Database Select US
Database Select Vehicle
Photos:
Photo Full Width
Photo Gallery
Photo Grid
Photo Carousel
Photo Album
Photo Filter
Photo Select
Photo Accordion
Photo Zoom
Photo Scroll

Quizzes:
Web Design Quiz x3
Web Design Logo Quiz x3
Web Coding Quiz x10
Web Development Logo Quiz x10
Graphics:
Graphic Design
Image Formats
Images Per Page
Material Cards
Search Engines
Browser Tier List
Magnify Window
Large Language Models
Autonomous Companies
Website Standards
Plethora:
Technology Chart
Parsing Python Scripts
Frameworks
Shopping Cart
Website Standards
AJAX Interactive XML
W3C
XHTML
Website Coding
Fediverse
About Eddie Jester